Our Services
Comprehensive PKI and cryptographic trust services for modern digital infrastructure
Homomorphic Encryption Engine
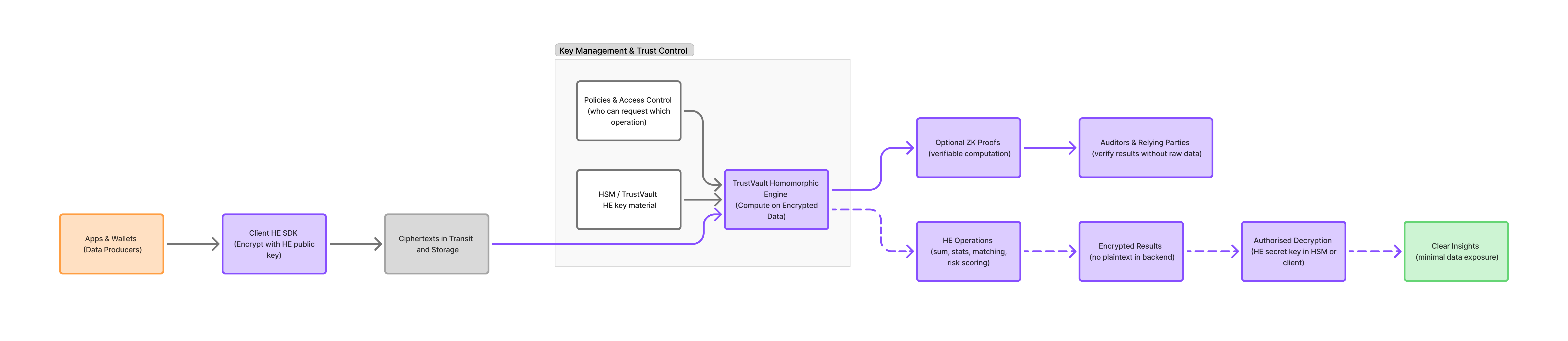
Homomorphic Encryption Engine - Privacy-preserving computation on encrypted data
TrustVault's Homomorphic Encryption Engine enables privacy-preserving computation and analytics on encrypted data. Organizations can perform calculations, analytics, and processing on sensitive data without ever decrypting it, maintaining end-to-end confidentiality while enabling valuable insights.
Core Capabilities
- Encrypted Analytics: Perform statistical analysis, aggregations, and computations directly on encrypted data without exposing plaintext
- Privacy-Preserving Processing: Enable data sharing and collaborative analytics while maintaining data sovereignty and privacy requirements
- Compliance-Friendly Architecture: Meet GDPR and data protection requirements by ensuring sensitive data remains encrypted throughout processing pipelines
- HSM Integration: Homomorphic encryption keys protected within Hardware Security Modules for maximum security
Use Cases
- Healthcare Analytics: Analyze patient data across institutions without exposing individual health records
- Financial Risk Analysis: Perform credit scoring and fraud detection on encrypted financial data
- Government Services: Enable cross-agency analytics while maintaining citizen privacy and data protection
- Enterprise Intelligence: Analyze sensitive business data without exposing trade secrets or confidential information
PKI & Certificate Services
TrustVault provides comprehensive Public Key Infrastructure and certificate lifecycle management services designed for modern trust requirements.
Certificate Issuance & Management
- TLS/SSL Certificates: Server authentication certificates for web services, APIs, and internal systems with automated renewal capabilities
- Client Authentication: Device, application, and user certificates for mutual TLS and zero-trust architectures
- Document & Code Signing: Capabilities for signing documents, software artifacts, and firmware (available as designed capabilities; deployment subject to specific requirements)
- Certificate Lifecycle: Complete management from issuance through renewal, revocation, and archival with CRL and OCSP support
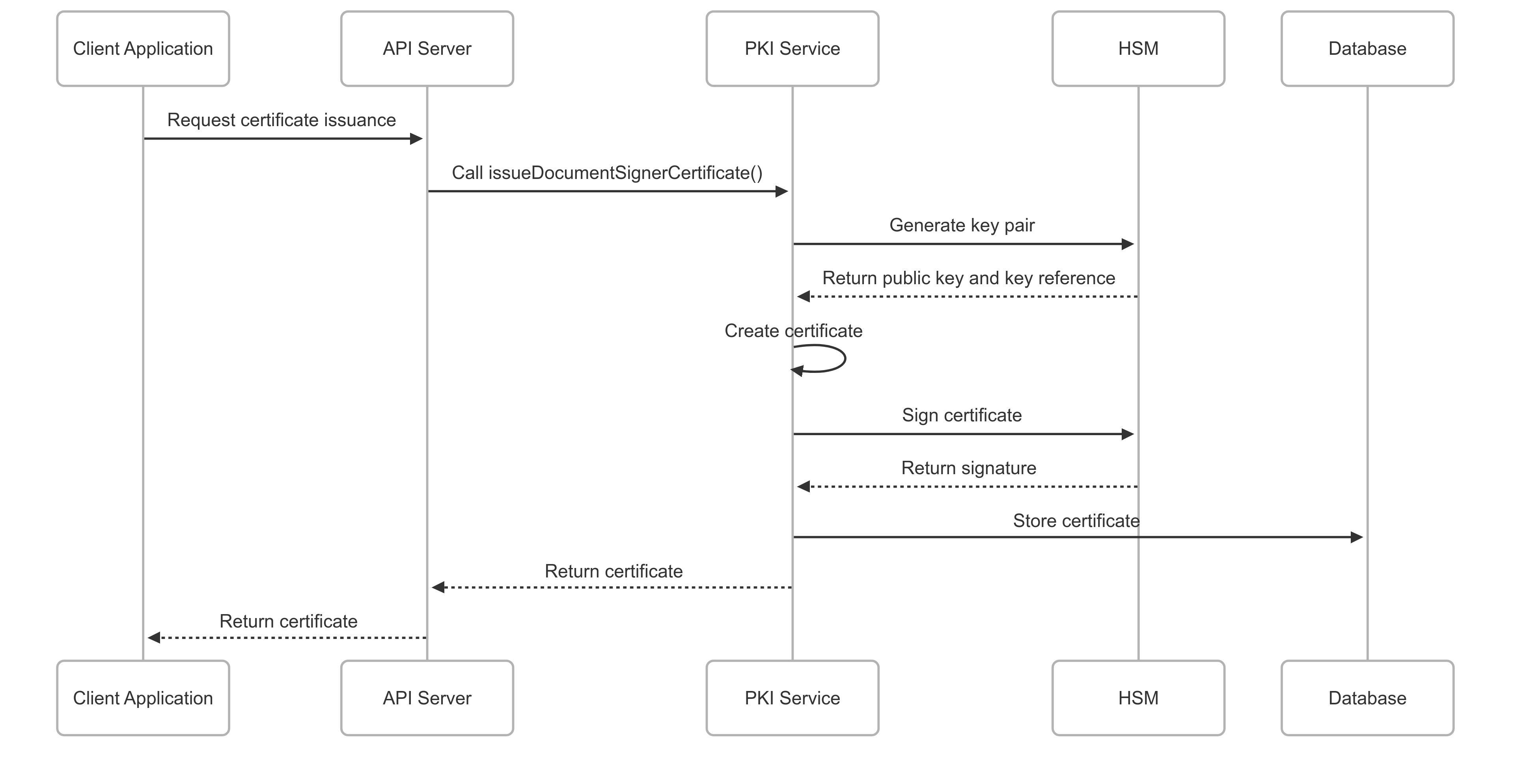
Certificate Issuance Process
PKI Hierarchy Management
We support flexible PKI topologies including traditional hierarchical models (Root → Intermediate → Issuing CA) and modern distributed trust architectures. Our infrastructure enables both internal enterprise PKI and integration with external trust frameworks.
 with Validation.png)
PKI Hierarchy with Validation Flows
PKI Service Topology
TrustVault's PKI infrastructure is built on a comprehensive service topology ensuring security, monitoring, and high availability:
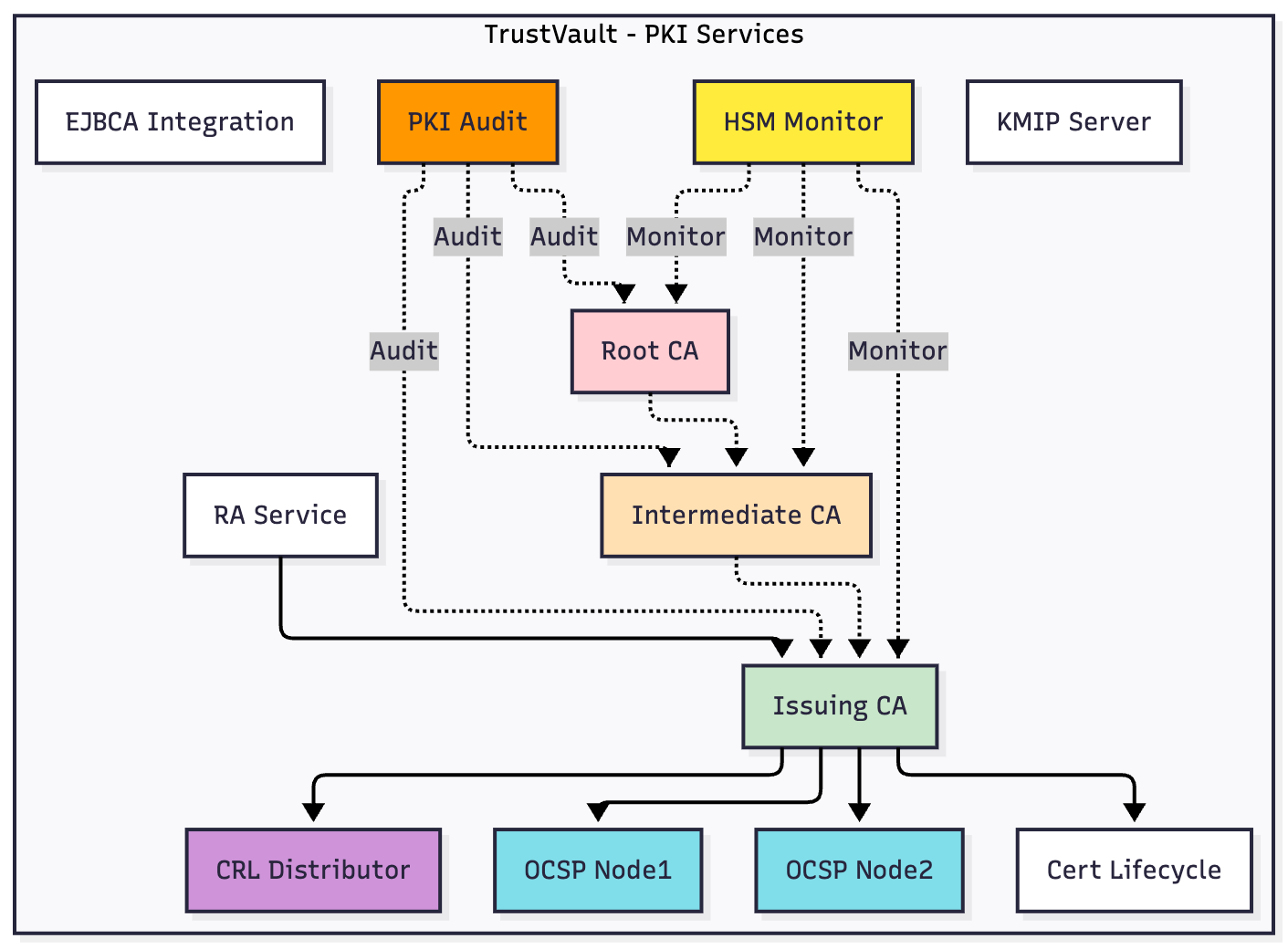
TrustVault PKI Service Topology - Complete infrastructure with CA hierarchy, monitoring, and certificate services
PKI Infrastructure Components
Certificate Authority Hierarchy:
- Root CA: Offline root certificate authority providing the trust anchor for the PKI hierarchy
- Intermediate CA: Operational intermediate CA bridging root and issuing CAs with configurable policy constraints
- Issuing CA: Online issuing CA handling day-to-day certificate issuance for end entities
Supporting Services:
- EJBCA Integration: Enterprise JavaBeans Certificate Authority integration for advanced PKI operations
- PKI Audit: Comprehensive audit logging for all certificate operations and CA actions
- HSM Monitor: Real-time monitoring of Hardware Security Module health and performance
- KMIP Server: Key Management Interoperability Protocol server for enterprise key management
- RA Service: Registration Authority service for identity verification and certificate request validation
Certificate Validation Services:
- CRL Distributor: Certificate Revocation List distribution for offline validation
- OCSP Node 1 & 2: Redundant Online Certificate Status Protocol responders for real-time certificate validation
- Cert Lifecycle: Automated certificate lifecycle management including renewal notifications and expiry handling
Monitoring & Audit Integration:
- PKI Audit monitors Root CA, Intermediate CA, and RA Service operations
- HSM Monitor tracks Root CA and Intermediate CA cryptographic operations
- KMIP Server monitors Intermediate CA and Issuing CA key management
- Complete audit trails for compliance and forensic analysis
Key Management & HSM Services
All cryptographic keys are protected using certified Hardware Security Modules, ensuring key material never exists in unprotected form.
HSM-Backed Key Operations
- Key Generation: Cryptographically secure key generation within HSM boundaries supporting RSA (2048, 4096 bit) and ECC (P-256, P-384, P-521)
- Secure Storage: Keys stored exclusively within HSM-protected storage, with hardware-enforced access controls
- Key Lifecycle Management: Comprehensive lifecycle including generation, activation, rotation, archival, and certified destruction
- Post-Quantum Readiness: Architecture designed to support PQC algorithms as HSM vendors implement standardized algorithms
HSM Pool Architecture
TrustVault employs a sophisticated HSM Pool architecture providing high availability, automatic failover, and future-proof cryptographic capabilities.
HSM Pool Components:
- HSM1 (Failover 2): Primary Utimaco CryptoServer for production cryptographic operations
- HSM2 (Failover 1): Secondary Utimaco CryptoServer for automatic failover and load balancing
- HSM3 (Failover 3): Tertiary HSM ensuring continuous operation even during maintenance
- Post-Quantum Crypto HSM: Dedicated HSM for PQC algorithm support and hybrid cryptography
- YubiHSM: Compact HSM for specific use cases and development environments
Failover & High Availability:
- Automatic failover between HSMs with no service interruption
- Load distribution across multiple HSMs for performance
- Hot-standby configuration ensures zero downtime
- Geographic distribution option for disaster recovery
Standards & Integration:
- PKCS#11 interface for vendor-independent cryptographic operations
- FIPS 140-2 Level 3 (or equivalent) certified hardware
- KMIP (Key Management Interoperability Protocol) for enterprise integration
- Key backup and disaster recovery with encrypted key wrapping
Encryption Standards Support
Beyond basic key management, TrustVault supports advanced encryption requirements:
- Transparent Data Encryption (TDE): Database-layer encryption with HSM-backed master keys
- KMIP Integration: Enterprise key management interoperability for multi-vendor environments
- Format-Preserving Encryption: Encrypt sensitive data while maintaining format and length
Advanced Cryptographic Services
Homomorphic Encryption as a Service (HEaaS)
TrustVault provides Homomorphic Encryption capabilities enabling privacy-preserving computation on encrypted data without requiring decryption.
Key Features:
- Secure Multi-Party Computation: Enable collaborative analytics across organizational boundaries without exposing raw data
- Privacy-Preserving Analytics: Perform calculations on encrypted datasets while maintaining confidentiality
- Regulatory Compliance: Meet GDPR data minimization requirements by computing on encrypted personal data
- Cloud Security: Process sensitive data in untrusted cloud environments while maintaining encryption
- Healthcare & Finance: Ideal for sectors requiring computation on highly sensitive data
Use Cases:
- Encrypted database queries and searches
- Privacy-preserving machine learning and AI model training
- Secure data aggregation across multiple parties
- Confidential financial calculations and risk analysis
Tokenization as a Service (TaaS)
Replace sensitive data with non-sensitive tokens while maintaining HSM-backed security for the mapping between tokens and original values.
Key Features:
- Format-Preserving Tokenization: Tokens maintain the same format as original data (e.g., credit card numbers, account IDs)
- Vaultless Tokenization: Stateless token generation using cryptographic algorithms, no database required
- Vault-Based Tokenization: Secure token-to-data mapping stored in HSM-protected vault
- Reversible & Irreversible Tokens: Choose between detokenization capabilities based on use case
- PCI DSS Compliance: Reduce PCI scope by tokenizing payment card data
- GDPR Support: Tokenize personal data to minimize exposure and support pseudonymization requirements
Use Cases:
- Payment card tokenization for e-commerce and retail
- Personal identifier tokenization (SSN, passport numbers, healthcare IDs)
- Database column-level tokenization for sensitive fields
- API security - tokenize sensitive parameters in transit
- Test data generation - create realistic but non-sensitive test datasets
PKI as a Service (PKIaaS)
Fully managed Public Key Infrastructure delivered as a cloud service, eliminating the complexity of operating your own certificate authority.
Key Features:
- Managed Certificate Authority: Root and intermediate CA operations managed by TrustVault
- Automated Certificate Lifecycle: Issuance, renewal, revocation, and expiry management
- ACME Protocol Support: Automated Certificate Management Environment for DevOps integration
- REST API Access: Programmatic certificate management for automation and CI/CD pipelines
- Multi-Tenancy: Isolated PKI hierarchies for different departments or customers
- HSM-Backed CA Keys: Root and intermediate CA private keys protected in certified HSMs
- Compliance Ready: Designed to support WebTrust, eIDAS, and other trust framework requirements
Certificate Types:
- TLS/SSL certificates for web servers and APIs (public and private)
- Client authentication certificates for users, devices, and applications
- Code signing certificates for software and firmware
- Document signing certificates for PDF and office documents
- Email certificates (S/MIME) for encrypted and signed email
- IoT device certificates for equipment authentication
Benefits:
- Reduced Complexity: No need to deploy and maintain CA infrastructure
- Cost Effective: Pay-per-certificate pricing eliminates capital expenditure
- Scalability: Automatically scales from hundreds to millions of certificates
- High Availability: Redundant infrastructure with SLA guarantees
- Rapid Deployment: PKI operational in hours, not months
Trust & Lifecycle Management
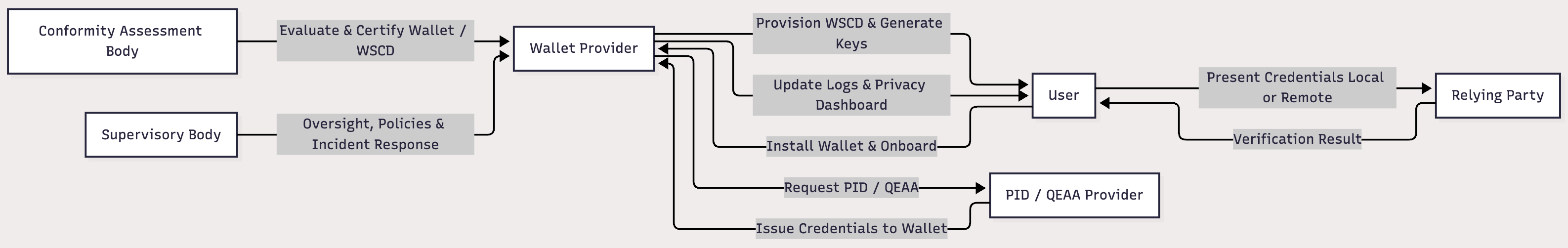
Complete trust and lifecycle management flow across TrustVault services
Advisory & Integration Support
Beyond core cryptographic services, we provide guidance and support for integrating TrustVault into your existing infrastructure.
Integration Services
- API integration guidance and sample implementations
- Certificate enrollment automation (ACME, SCEP, EST protocols)
- PKI policy and certificate profile design
- HSM selection and deployment planning
Cryptographic Best Practices
We provide recommendations on key management, algorithm selection, key rotation schedules, and cryptographic hygiene aligned with industry standards and regulatory requirements. These recommendations are advisory in nature and should be evaluated within your specific organizational and regulatory context.
Interested in Our Services?
Contact us to discuss your PKI and trust infrastructure requirements.
Contact Us